
A couple of weeks ago, I began to see signs that someone was attempting to attack my online profiles and accounts. Rather than wait until my security had been broken, I decided to take steps to get out ahead of the hacker by adding additional layers of protection to my accounts and reading up on the latest best practices in online safety. "An once of Prevention is worth a pound of Cure," as Poor Richard said. In this article, I will share some of what I have learned and offer some free advice and tools to help you.
Fear Not!
If you find yourself under cyber attack, you absolutely must not panic! Fear and anger are powerful emotions that have little fellowship with the cool logic you're going to need to defend yourself. Channeled properly, they can be great friends to have in a fistfight, but they're your second most dangerous enemy in this kind of battle.
If you find your heart beating hard, your face heating up, your thinking muddled, and you just want to either crawl into bed and hide or lash out at someone, then you're in no state to make rational decisions. Use whatever means are at your disposal to calm yourself—meditation, prayer, talking with a friend, taking a walk, whatever. If your coping mechanism involves alcohol or other chemical aids, though, I recommend waiting until they wear off before acting.
If you find you just can't calm yourself, ask a trusted friend to help you. You definitely need someone who is fully in control and thinking clearly to be in the driver's seat. Your emotions are valid—I don't want to discount them at all. It's okay to be angry or afraid, but those feelings will do more harm than good if they guide your response to a hack.
Two possible consequences of acting while in the grip of emotion: 1) Creating new vulnerabilities that might actually be worse than the old ones. 2) Accidentally locking yourself out of an account. That second one is something I've done to myself on more than one occasion.
Detecting a Hacker
When the trees are seen to move, the enemy is advancing.
—Sun Tzu
The first indicator that I was under attack was an alert from Steam that someone had logged into my account from the Tamil province in India. Fortunately, I had two-factor authentication enabled, so they were unable to get all the way in. A few days later, I got a notice about login attempts at my bank, then Facebook. Although I had neglected two-factor protection for both of those accounts, I had hardened them with unique, random passwords (more about passwords in a bit), so neither was compromised. There was also an email from the Department of Education that someone had used my email address on the FAFSA.

Depending on the chosen methods employed by the hacker and their end goal, there may be other signs, but seeing them can be difficult without the right tools. For a hacker intent on accessing your finances or stealing your identity, the best way to spot them is by closely monitoring your credit. If you're an American, you are entitled to an annual free copy of your credit reports from all three of the bureaus: Transunion, Equifax and Experian. If you're seeing signs of identity theft, it's tempting to grab all three at once, but a more reasoned strategy is to spread out your requests throughout the year so you can get more continuity of information. The correct website to use is https://www.annualcreditreport.com. Any other website may or may not be trustworthy, but that one is official. And although that's a link you see there, I recommend not even clicking it, but copying and pasting that text into your location bar. When your identity is at stake, Trust No One. Not even me. While you're getting your report, take the opportunity to put a fraud alert on them. This prompts anyone who pulls your report to be extra careful in verifying your identity. It won't stop you from getting new credit, but it will make it more difficult for someone who isn't you to open a new card. For even more protection, you can freeze your credit instead, which will prevent you from opening new accounts. It's up to you whether the extra security is worth the inconvenience of needing to unfreeze. Remember that this will affect things like setting up an account with the electric company.
A credit monitoring service such as Credit Karma can help you to keep an eye on your credit reports and score continuously. Credit Karma is supported by affiliate marketing—they make their money when their users get a credit card through one of their links. There are other monitoring services that charge you directly, such as Zendough. There is some inherent danger in using such a service because you are, after all, giving them enough information to identify you definitively to the credit bureaus. See the above image. A bad actor at a credit monitoring service could theoretically have access to enough information about you to do great damage. I'll have a little bit more to say on this topic a little further down, when I talk about managing risk.
Credit monitoring can really only catch new accounts and applications. It won't tell you if someone is using your current accounts. For that, you need to be able to see what's going on in your accounts on a daily basis. I use Mint, which tracks all of my account balances and shows me transactions, aggregated or separated by account. It also has a number of other useful tools, such as automatic budgeting help, savings calculators, and reports to help you analyze your financial situation. Again, there is some risk to using it because you need to give it permission to access all of your accounts. If that weirds you out too much, you can get all of the same information by logging into your banks' websites directly. In any case, you should be checking your transaction history daily as long as you feel you're under threat.
UPDATE Feb 2024: I no longer use Mint. I've been feeling uncertain about them ever since they started letting me bypass my own password by logging in with my phone. Which is also my 2-factor auth device. That seems super insecure to me, so I'd been considering jumping ship for some time. When Intuit started rearranging their branding to put Mint under Credit Karma, the uncertainty become too much for me to bear, and I canceled my memberships for both services. I have not decided yet if I will sign up for another aggregator. I'm feeling risk-averse at the moment. When you make a decision like this, it's very important to know how you're going to fill the intelligence holes. I'm not going to have daily access to my credit score for the time being, so I'll have to watch my annual reports more closely.
An identity protection service is also a good idea. These services monitor sources of leaked data and can alert you if information about you appears in a leak. I'd hazard a guess that virtually every American has been offered some degree of free identity theft protection in response to a data breach at some point. I've had several offers and accepted one made by the US Government's Office of Personnel Management.
If you operate a website of any kind, but especially a blog, look into tools to alert you to unusual activity. Watch your stats; an increase in accesses from countries you don't normally deal with—particularly Russia, Ukraine, Turkey, China, and India—can be a sign of trouble. If you run a WordPress site, the Wordfence plug-in can monitor intrusion attempts. I won't link to Wordfence here—you should search for it through the Plugins link on your WordPress control panel to ensure you have the official, trusted plug-in.
There are sometimes social indicators of a problem, as well. If family members start getting odd calls asking them to verify information related to your background, such as what high school you went to or previous addresses you've lived at, that's a sign that somebody might be trying to gather answers to security questions. If you don't yet realize that you're in someone's crosshairs, such inquiries might never get your attention—how likely is your sister to call you to say that someone was asking about family pets? If you do know that an attack is in progress, it's not a bad idea to let your loved ones know about it so they can be a little bit more vigilant about the information they share.
Risk Awareness
 There is no such thing as perfect security. A determined enough hacker with sufficient resources can eventually crack anything. The advice I'm giving here isn't likely to stop fsociety. The name of the game is risk management. Are you safer with more information or less exposure? Is the likelihood of your password manager being compromised greater than your accounts getting accessed because you used the same password everywhere? You have to make compromises somewhere; just be aware of exactly what those compromises are and how to mitigate them if they should become an issue.
There is no such thing as perfect security. A determined enough hacker with sufficient resources can eventually crack anything. The advice I'm giving here isn't likely to stop fsociety. The name of the game is risk management. Are you safer with more information or less exposure? Is the likelihood of your password manager being compromised greater than your accounts getting accessed because you used the same password everywhere? You have to make compromises somewhere; just be aware of exactly what those compromises are and how to mitigate them if they should become an issue.
I mentioned above that there is some risk in giving Credit Karma or Mint so much information about yourself. The risk there is that some insider at one of those companies could use that information for evil, or they could be subject to a data breach. Such a risk is systemic—it's almost certainly going to affect everyone equally. It is very unlikely that a hacker targeting you specifically is going to gain employment at Intuit for the purpose of compromising Mint or Turbo Tax just so they can wipe you out. I mean, if someone really is going to all that trouble over you, then you seriously need to rethink your relationships! It makes a great TV show, but it really isn't very likely.
Since we're talking about an attack directed against you personally, even if it's part of a wider criminal operation, a systemic threat is usually less risky than the alternatives. Don't give yourself an ulcer over it, though. If you experience a lot of anxiety over giving up information to Intuit, then listen to your instincts and don't sign up for Mint. Again, though, try not to let your fear rule your reactions. When you do, you're giving control to the enemy, letting the hacker dictate the terms of the engagement.
Stay aware of any data breaches disclosed by companies you deal with—the information leaked in such a breach is often sold, or even posted freely, on the dark web, and it's easily searchable. Even if you're using an identity protection service, don't assume you're safe just because you didn't get an alert.
Armor Up!
Even in the midst of an attack, you still have a significant advantage. Your enemy must do a lot of guesswork about where you have accounts, what your credentials might be, and how to answer security questions. You, on the other hand, already know all that information, and you can change it much faster than the hacker can discover it. The key to fortifying successfully, though, is to have a plan and stay organized. If you get into too big a hurry, you can create more problems than you solve by replacing strong, but possibly compromised, passwords with unknown but much weaker ones.

The Keymaster — Password Management
The first tool you should reach for, and I hope you're already using it, is a secure password manager. I use LastPass. It has a web interface, browser extensions for all of the major browsers, and a mobile app. UPDATE 2022: LastPass has had some problems. The encrypted vaults of all of their customers was stolen, and they didn't do enough to mitigate the damage. In addition, although the credentials inside the vaults are encrypted, the URLs are not, so the advice I gave above about an attacker not knowing which sites to target is weaker if you've been using LastPass. At this time, I recommend looking at the commentary on various other password managers and choosing one based on recommendations from security professionals. UPDATE 2025: I've settled on BitWarden.
A password manager can help you generate unique and strong passwords for every site you use, keep track of them, and automatically fill out web forms for you. You can see and manage remote sessions, allowing you to turn off access if someone steals your laptop or phone while you're logged in.
Unfortunately, there is some risk in using a browser extension to manage your passwords. Any vulnerabilities in the extension can expose all of the stored passwords. A safer method would be to use a desktop-based app from which you can copy and paste your credentials. Personally, I find the danger of possible extension security flaws to be much smaller than that posed by my own laziness. If your memory is good enough to manage credentials for a very small number of sites, you might be able to get the best of both worlds by using the password manager for the bulk of your log ins, but your own memory for two or three critical ones, like your main email and your banks. The more spread out your critical resources are, though, the less attractive that option gets.
There is also some risk of an attacker breaking your master password and getting access to everything it protects. It's no good protecting Amazon with a password like H50sdW%INYSqS%3b if the master password is "FeistySquirrel8." LastPass and BitWarden don't seem to have any limit on the length of a password, though, so consider using a pass phrase instead of a pass word. It will take years for a brute force attack to crack "His name is Bobo. He knows no mercy." The longer the phrase is, the more secure it is. Every additional character increases the security exponentially.

Another option is to use some personal encryption method to choose your passwords. I have an acquaintance who has some kind of formula to turn a website's address into a password. I don't know exactly what his algorithm is (that would defeat the purpose of using it, after all), but he seems to trust it. I don't know what he does when he has to change one.
Username Obfuscation
Like most people, I am in the habit of using my primary email address for most website registrations. If I expect that one of them will give me a lot of spam, I have a throwaway address I use for that. Unfortunately, doing this weakens the potential security of every account by 50%. Everyone who knows me or knows of me knows what my email address is, and so they know half of my login credentials for every website I use. For sites that use nicknames instead of email addresses, I use the same two screen names pretty much everywhere. There may well be more people in the world who know me as Midgardsormr than who know me as Bryan.
As I continue to harden my accounts, though, I am shifting them to a new email address used only for my most sensitive accounts. I'll never use it for communication, either personal or professional. I'll never connect it to any social media account or otherwise expose its relationship to me. By doing so, I can reduce the chances that someone can guess my credentials, and I can ensure that even if someone busts my main email, they still can't get to my banks.
Where possible, I am changing my user name to something not easily guessed, as well. On many sites, the user name is also the screen name, so I can't do that everywhere unless I want to give up the handle I've been using since 1992. Still, there's no need to use that name to access my health insurance.
Two-Factor Authenticaion
This idea has almost become a buzz word lately. Everyone's about two-factor authentication, even when it doesn't make sense or even weakens a log-in. Here's a hint: If you are using the same device for password recovery and two-factor authentication, you haven't improved your security. It just ensures that someone who has your phone can definitely get into your account but if you're sitting at your desk without the phone, you can't.
However, two-factor authentication, when done right, is a massive advantage in securing your accounts. If you've never used it before, the idea is that you need both your password and a short numerical code to log in. The code is usually delivered by email or text message. There are also some sites that permit you to use an authenticator app on your phone, which generates a code using a synchronized rolling encryption. So long as it is not possible to use the same device or account to get both the password and the code, your account will remain secure.
Besides the occasional poor implementation of the system, the other major vulnerability is your phone. A hacker who manages to clone or snoop on your phone can intercept the code. The number of attack vectors on the typical phone is frightening, really. The carrier's website and customer service department, bluetooth, wi-fi, malicious applications and web sites, and outright physical theft are all dangers when you rely too heavily on your phone for security. Plus, you can probably read your email on your phone, so even if your two-factor scheme delivers the password to email and the auth code by SMS, someone who has your phone still gets both! Another reason to use that dedicated log-ins email—and to always log out if you're not actively using it.
In conclusion, use two-factor authentication, but don't expect it to be a panacea.
Security Questions
One of the most problematic features of most services' log-in systems is password recovery through use of secret questions. If someone is coming after you, getting the answers to many of your secret questions is a matter of a background check and browsing your Facebook. Why are we still using mother's maiden name as a way of verifying identity? Everyone's mother is on Facebook! My mother even uses her maiden name as part of her identity there so old high school friends can find her.
You can immediately improve the security of your accounts by giving false answers to those questions. Favorite sports team: Androcles. City where you met your spouse: Birdwatching. Or you can use your password manager to generate a random string and use that as your answer. Use the Notes field of your password manager to store that information. It's a little inconvenient at times, but it's better than just handing your keys to every random stranger.
Social Engineering Defenses
A hacker attempting to divine your answers to secret questions is probably going to need to employ some so-called "social engineering." Usually, the weakest part of any cyber defense is the people involved. And other people are almost entirely outside of your ability to modify. So what is to be done?
First thing: If you think you're being hacked, alert your friends and family. Let them know that if a stranger seems very interested in their history ("Where were you living in 1998?" "I had a great dog when I was a kid. Did your kids have a favorite pet?"), they should avoid answering.
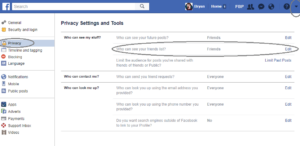 You should also close off access to your contacts. On Facebook, go to your privacy settings and set "Who can see your friends list?" to "Friends" or less. Check the other privacy settings while you're in there to make sure you're comfortable with them. You want to make it as difficult as possible for your attacker to find the people who could answer questions about you or provide them with access.
You should also close off access to your contacts. On Facebook, go to your privacy settings and set "Who can see your friends list?" to "Friends" or less. Check the other privacy settings while you're in there to make sure you're comfortable with them. You want to make it as difficult as possible for your attacker to find the people who could answer questions about you or provide them with access.
Facebook also has a "Trusted Contacts" feature where you can designate up to five people who can help you get back into your account if you get locked out. Those people absolutely must be made aware of the threat. Make sure they know how you will contact them if you need them, and if you're really paranoid, you could even set up verbal passwords. "If it's really me, I'll identify myself with the word 'marmalade.'" You should also consider choosing people that a stranger might not guess. Parents and siblings are obvious choices, but who's going to guess your high school band director?
Another social engineering technique that I'm sure you've seen is phishing. You receive an email apparently from your bank or your email provider saying that they need to verify some information and please to click this link. These phishing emails are usually pretty easy to spot—they'll come from someone's university email address, have misspellings or clumsy grammar, and the links don't lead to the right place. I've seen some very impressive ones, though, that exactly mimic a real bank's emails, to the point of using the CSS from the bank itself! The links might take you to a login page at bankofamerican.com or something of the sort and have an exact replica of the bank's real page. The most sophisticated phishing scheme I've yet heard of even had a mechanism to forward the credentials to the real bank, so the victim never even knew they were anyplace other than the correct website, but the thieves had the password!
UPDATE January 2023: Malefactors have also begun exploiting ad placement in Google search results. These false ads look like search results and are placed at the top of the listings. Such an ad leads to a site with an address very similar to the real one, such as www.1passwordapp.com rather than www.1password.com. I recommend installing an ad suppressor in order to remove these results from view entirely so you can never be fooled into clicking one. I am currently using uBlock Origin.

I've taken a screenshot of an email I received today. It looks exactly like an official Chase email, including much of the typical language the bank uses in its communications. However, the email address it came from is incorrect. Any Chase-originated email would come from the chase.com domain, not email.com. The links in the email all lead to what looks like a Canadian personal website. And there are the usual giveaways in grammar: What should be a list with bullets instead uses a double-hyphen, and the third line starts with a period. In addition, this sentence is a little bit clumsy, is missing a space, and has an inappropriate capitalization: "For these reasons and to further protect your identity and personal information,We immediately require that you click here to verify your Chase Online Banking."
Although grammar and layout errors like those are usually a giveaway, the most sophisticated attackers will take more care in crafting an email that looks completely legitimate. I was almost taken in by one ostensibly from Amazon—it was virtually flawless, except that it came to an address I don't use for Amazon.
The best defense against phishing is to never click links in email. If I get a note from my bank, I type the bank's url into my browser myself, even if I'm 102% sure that it's a legitimate message. There are some exceptions to this rule. For instance, verification links are usually too long to retype, and they usually come as a direct result of a request on your part, so those are probably safe.
Another psych-ops threat is the use of "confidential" information to establish trust. Data breaches don't expose just email addresses and passwords. They can also leak P.O. numbers, credit card records, work order descriptions, and an unlimited variety of other information a company might keep on file. If your information has been exposed in such a breach, a hacker can obtain it and use it against you. My boss got a phone call supposedly from Dell inquiring about a recent service request for his computer. The scammer had the date of the service, the model of the computer, a description of the work done, and likely more information. To defend yourself against this kind of attack, develop for yourself a policy and a habit: Someone may initiate contact with you, or they may ask for private information. They may not do both. If someone calls you and asks you to confirm your birthdate or some-such, even if they've already proved they have other information, decline and offer to call back at the number provided by a website or your insurance card or whatever. (This advice courtesy of Peter from Saving the Game.)
There are other psychological tactics that might be used, but they're more the province of con artists than hackers. Strategies for dealing with them go back to Agent Mulder's advice given above. Add to that "If it seems too good to be true, it probably is" and "But I didn't buy a lottery ticket!"
Hardening your Web Site
Most of my advice has been related to an attacker trying to compromise your social media and banking accounts. Those are the assets they are most likely going to be able to turn into money. Your website is a less valuable target, unless you're running an e-commerce site, but it may still be attacked. A hacker can use a compromised web site to launch spam attacks, to inject malicious code into visitors' browsers, or to cheat search engine algorithms by pointing thousands of websites to the one the hacker wants to optimize. At one point there was even a botnet using WordPress sites to mine cryptocurrency! (An insanely inefficient method costing far more electricity than it earned.) So you should take some steps to make sure you're protected on that front, as well.
If you operate a blog on WordPress.com you probably don't have much to worry about other than simply losing access to it. You're protected by the umbrella of WordPress' own security. I am not sure if you have the same options for plug-ins there as you do on a standalone installation like mine, but check these recommendations out.
My understanding of web security is somewhat primitive. I do my best to follow the best practices that I am aware of, but please be aware that this is by no means a thorough guide. To prevent a brute force attack, I use a plug-in called Loginizer. After a certain number of failed log in attempts, it will lock out the IP address from which those attempts originated. It can be used to blacklist IPs or IP ranges. On the advice of my friend Jolene, the Bootstrap Blogger, I also installed Wordfence. I don't think my web sites are being attacked, though, so I'm not sure how to measure its effectiveness.
Check the permissions of all of your files and directories using whatever administration panel you have access to. Any file with permissions higher than 644 or directories higher than 755 should be examined carefully to find out why they're so permissive. If you're not familiar with Unix/Linux permissions, the three numbers represent the file's owner (usually the web server itself is the owner), authenticated users (you or your web developer), and the unwashed masses. A 7 indicates the ability to execute code, a 5 the ability to write, and 4 is read-only.
Beyond permissions and not installing modules from questionable sources, that's about as far as I can take you in terms of web security. It should be enough to protect you from most threats, though.
General Internet Safety
You should also take the time to make sure your personal computer is not leaking information. Use a secure operating system—Windows XP was great in its time, but if you're still running it you're playing with fire. Windows 10 seems to be a pretty solid and useful OS so far. If you're on anything earlier than 7, it's time to move up.
Run anti-virus. I currently recommend Panda Security if you're on Windows (UPDATE January 2023: I haven't evaluated anti-virus in a while; I'm now using Cylance, a paid service). There's a free version that doesn't eat up too many system resources. UPDATE 2025: Cylance discontinued their free offering. I've been (possibly unwisely) depending on the built-in Defender anti-virus that comes with Windows. Current sentiment among non-corporate users is that Defender is adequate protection. I am unconvinced but have been too lazy and cheap to look for something else. Supplement the anti-virus with a good ad-ware scanner like Malwarebytes. Even if you're on a Mac, anti-virus is still important, but I don't know the options there.
Be careful which websites you visit. Don't run applications from sources you don't trust. For heaven's sake, don't run pirated software of any kind! A software pirate is, by definition, a criminal. Do you really think they can be trusted not to install a keylogger on your computer? Don't click on links that arrive by email, even if it's from someone you know. I receive mail on a weekly basis from contacts whose email accounts have been compromised. And never ever run an executable file delivered by email! Even simple documents and pictures can be vectors for an attack, so be careful with all attachments. If you weren't expecting to receive a file, it's likely dangerous. Double check with the sender using a different means of contact to verify a file's legitimacy.
Use a good cloud backup service to protect your data. I have in the past recommended Crashplan, but they're discontinuing the Home version of their service, and I haven't yet found another that I like. But if you're looking for some possibilities: Backblaze, Carbonite and iDrive.
UPDATE January 2023: I'm now using the Glacier product from Amazon Web Services. I don't know how difficult it is to set up for most users, but my Synology network storage server has an application that made it very easy. It's slightly more expensive than Crashplan was, but I'm much more confident that Amazon's not going to disappear suddenly.
Don't use hardware you find in the street. It's tempting to grab that nice USB cable or thumb drive that someone dropped, but even something as simple as a USB cable can carry a malicious payload. Here's an example of one that's available on the open market: https://shop.hak5.org/products/omg-cable
Personal and Physical Security
All the cyber security in the world can't help you if you leave the door to your house unlocked. I have a few extra steps that I take in my day-to-day life out under the sun: Always lock your door. Engage a password-protected screen saver on your computer when you're not home. Carry a decoy wallet in case you get mugged. Don't walk down dark alleys at night in Hollywood. Decide on a pass phrase you can use to verify your identity in case you travel back in time and have to give yourself some valuable information. Put together a "bug out bag." Decide on a rally point location in case you are separated from your group (I use the local 1st Baptist Church. Almost every community in the U.S. has one). Stay aware of your surroundings. Look both ways before you cross the street.
Resources
In the course of putting together this guide, I did a lot of reading in a lot of places. Here are some of them:
When Life Gives You Lemons: Pulling Myself out of a HACKED situation
https://www.theverge.com/2017/7/10/15946642/two-factor-authentication-online-security-mess
https://codex.wordpress.org/Hardening_WordPress
https://counterespionage.com/malicious-usb-cables/
If I find more, I'll link them here. Stay safe!
LastPass recently disclosed a security breach:
https://blog.lastpass.com/2022/08/notice-of-recent-security-incident/
tl;dr: No user information was exposed, and they believe their customers remain secure. Investigation into the breach is ongoing, but they believe they have bottled up any vulnerabilities it caused. The ongoing threat is that some of their proprietary technology was stolen, which might enable someone to engineer a new attack based on knowledge of the current system.